Azure Active Directory: 7 Ultimate Power Tips for 2024
Welcome to the ultimate guide on Azure Active Directory! Whether you’re a seasoned IT pro or just starting your cloud journey, this comprehensive breakdown will demystify everything about Microsoft’s identity and access management powerhouse.
What Is Azure Active Directory and Why It Matters

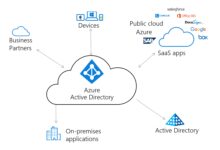
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service, designed to help organizations securely manage user identities and control access to applications, data, and resources. Unlike its on-premises predecessor, Windows Server Active Directory, Azure AD is built for the modern, cloud-first world.
Core Definition and Evolution
Azure Active Directory was launched in 2010 as Windows Azure Platform AppFabric Access Control Service and evolved into a full-fledged identity platform. Today, it’s a critical component of Microsoft Entra, Microsoft’s broader identity and security suite. Azure AD enables single sign-on (SSO), multi-factor authentication (MFA), conditional access, and identity governance across cloud and hybrid environments.
- Originally focused on cloud app access, now central to Zero Trust security models.
- Supports over 1.4 billion users and millions of organizations globally.
- Integrates seamlessly with Microsoft 365, Azure, and thousands of third-party SaaS apps.
“Azure Active Directory is the identity backbone of the Microsoft cloud ecosystem.” — Microsoft Tech Community
Key Differences Between Azure AD and On-Premises AD
Understanding the distinction between Azure Active Directory and traditional Active Directory (AD) is crucial for IT professionals managing hybrid environments. While both manage identities, their architectures, protocols, and use cases differ significantly.
- Architecture: On-prem AD uses LDAP, Kerberos, and NTLM; Azure AD relies on REST APIs, OAuth 2.0, OpenID Connect, and SAML.
- Deployment: On-prem AD runs on Windows Server domain controllers; Azure AD is cloud-native and globally distributed.
- Scalability: Azure AD scales automatically; on-prem AD requires manual infrastructure planning.
- Management: On-prem AD uses Group Policy; Azure AD uses Intune and Conditional Access policies.
For deeper technical comparison, visit Microsoft’s official documentation.
Core Features of Azure Active Directory
Azure Active Directory is packed with features that empower organizations to manage identities securely and efficiently. From authentication to governance, these capabilities form the foundation of modern identity management.
Single Sign-On (SSO) Across Cloud and On-Premises Apps
SSO is one of the most user-friendly and security-enhancing features of Azure Active Directory. It allows users to log in once and gain access to multiple applications without re-entering credentials.
- Supports SSO for Microsoft 365, Azure portal, Salesforce, Workday, and over 2,600 pre-integrated SaaS apps.
- Enables seamless access via SAML, OAuth, OpenID Connect, and password-based SSO.
- Reduces password fatigue and phishing risks by minimizing login prompts.
Learn more about SSO configurations at Microsoft Learn: Single Sign-On.
Multi-Factor Authentication (MFA) and Identity Protection
Security is paramount, and Azure AD’s MFA adds an essential layer of protection by requiring users to verify their identity using at least two methods.
- Available methods include phone calls, text messages, Microsoft Authenticator app, FIDO2 security keys, and biometrics.
- Azure AD Identity Protection uses AI to detect risky sign-ins and user behavior, triggering automated responses.
- Can enforce MFA based on risk level, location, device compliance, or application sensitivity.
“Organizations using MFA block over 99.9% of account compromise attacks.” — Microsoft Security Intelligence Report
Conditional Access: The Heart of Zero Trust Security
Conditional Access policies in Azure Active Directory allow organizations to enforce access controls based on specific conditions like user location, device compliance, sign-in risk, and application sensitivity.
- Example: Require MFA when accessing financial apps from outside the corporate network.
- Can block access from unmanaged devices or high-risk countries.
- Integrates with Microsoft Intune for device compliance checks.
Explore Conditional Access policies in depth at Microsoft Learn: Conditional Access.
Understanding Azure AD Editions: Free, P1, P2, and B2B
Azure Active Directory comes in four main editions: Free, Premium P1, Premium P2, and B2B (Business-to-Business). Each tier offers increasing levels of functionality, security, and governance.
Azure AD Free: The Foundation for All Organizations
Every Microsoft 365 or Azure subscription includes Azure AD Free at no additional cost. It provides essential identity and access features suitable for small to medium businesses.
- Basic SSO for cloud apps.
- User and group management.
- Self-service password reset (SSPR) for cloud users.
- Support for up to 50,000 directory objects (users, groups, contacts).
While limited, Azure AD Free is a solid starting point for organizations beginning their cloud journey.
Azure AD Premium P1: Enhanced Security and Automation
Premium P1 builds on the Free edition with advanced features focused on access management, automation, and security.
- Dynamic groups based on user attributes.
- Access reviews for periodic entitlement verification.
- Self-service application access via My Apps portal.
- Hybrid identity with password hash sync, pass-through authentication, and seamless SSO.
- Advanced reporting and monitoring.
P1 is ideal for organizations needing better access governance and hybrid identity support.
Azure AD Premium P2: Identity Governance and Risk Intelligence
Premium P2 includes all P1 features plus advanced identity protection and governance capabilities.
- Azure AD Identity Protection with risk-based policies.
- Privileged Identity Management (PIM) for just-in-time (JIT) access to administrative roles.
- Entitlement management for automated provisioning and lifecycle management of access packages.
- User risk detection and automated remediation workflows.
P2 is recommended for enterprises with strict compliance requirements and high-security needs.
Hybrid Identity: Bridging On-Premises and Cloud with Azure AD
For organizations with existing on-premises infrastructure, hybrid identity is a critical strategy. Azure Active Directory enables seamless integration between on-prem AD and the cloud, ensuring users have a consistent identity across environments.
Authentication Methods in Hybrid Environments
There are three primary methods for enabling authentication in hybrid scenarios:
- Password Hash Sync (PHS): Synchronizes password hashes from on-prem AD to Azure AD, allowing cloud authentication without requiring domain controllers online.
- Pass-Through Authentication (PTA): Validates user credentials against on-prem AD in real-time using lightweight agents.
- Federation with AD FS: Uses Active Directory Federation Services for SSO, though Microsoft recommends PHS or PTA for simplicity and reliability.
Microsoft recommends PHS or PTA over AD FS due to lower complexity and better cloud integration. Learn more at Choose the Right Authentication Method.
Azure AD Connect: The Synchronization Workhorse
Azure AD Connect is the tool used to synchronize identities from on-premises Active Directory to Azure Active Directory.
- Handles user, group, and contact synchronization.
- Supports password synchronization, group writeback, and device writeback.
- Can be configured for filtering, attribute flow customization, and staging mode.
- Requires regular updates and health monitoring.
Best practices include running Azure AD Connect on a dedicated server, enabling health monitoring, and using express settings for simple deployments.
“Azure AD Connect is the bridge between your legacy directory and the cloud future.” — Microsoft MVP Community
User and Group Management in Azure Active Directory
Effective user and group management is essential for maintaining security, compliance, and operational efficiency in Azure Active Directory.
Creating and Managing Users
Administrators can create and manage users directly in the Azure portal or via PowerShell and Microsoft Graph API.
- Users can be created manually, bulk uploaded via CSV, or synchronized from on-prem AD.
- Each user has a unique User Principal Name (UPN) and can be assigned licenses, roles, and group memberships.
- Self-service user provisioning is possible through Azure AD B2C or custom apps.
Best practice: Use role-based access control (RBAC) to assign minimal necessary permissions.
Static vs. Dynamic Groups
Groups in Azure AD simplify access management and policy application.
- Static Groups: Members are added manually. Ideal for small, stable teams.
- Dynamic Groups: Membership is based on rules (e.g., department = “Finance” or user type = “Guest”). Automatically updates as user attributes change.
Dynamic groups are available in Azure AD Premium P1 and are powerful for automating access control.
Role-Based Access Control (RBAC) and Privileged Identity Management
RBAC allows administrators to assign roles with specific permissions, reducing the risk of over-privileged accounts.
- Predefined roles include Global Administrator, User Administrator, Helpdesk Administrator, and more.
- Custom roles can be created for granular control.
- Privileged Identity Management (PIM) enables just-in-time (JIT) activation of administrative roles, reducing standing privileges.
PIM is a key feature in Azure AD Premium P2 and is critical for securing administrative access.
Security and Compliance in Azure Active Directory
Security is not an afterthought in Azure Active Directory—it’s built into its DNA. From threat detection to compliance reporting, Azure AD provides robust tools to protect your organization.
Identity Protection and Risk-Based Policies
Azure AD Identity Protection uses machine learning to detect suspicious activities such as sign-ins from unfamiliar locations, anonymous IP addresses, or impossible travel.
- Classifies risks as low, medium, or high.
- Can automatically require MFA, block access, or prompt password reset based on risk level.
- Integrates with Microsoft Sentinel for advanced threat hunting.
Enable Identity Protection in the Azure portal under Security > Identity Protection.
Conditional Access for Threat Mitigation
Conditional Access policies are the enforcement mechanism for security controls.
- Create policies that require compliant devices (via Intune) for accessing sensitive apps.
- Block legacy authentication protocols like IMAP/SMTP, which are prone to credential theft.
- Enforce MFA for guest users or when accessing from untrusted locations.
Best practice: Start with a baseline policy requiring MFA for all users and refine based on risk.
Compliance and Audit Logging
Azure AD provides extensive logging for sign-ins, audit activities, and directory changes.
- Sign-in logs show user activity, IP addresses, devices, and authentication methods.
- Audit logs track administrative actions like user creation, role assignment, and policy changes.
- Data can be exported to SIEM tools via Azure Monitor or Log Analytics.
For compliance frameworks like GDPR, HIPAA, or ISO 27001, Azure AD’s audit capabilities are invaluable.
Advanced Scenarios: B2B, B2C, and Identity Governance
Beyond internal identity management, Azure Active Directory supports external collaboration and customer identity scenarios.
Azure AD B2B: Secure Collaboration with External Partners
Azure AD B2B allows organizations to invite external users (partners, vendors, contractors) to access internal applications securely.
- Guest users sign in with their own work or personal accounts.
- Administrators control access via groups and Conditional Access policies.
- Self-service invitation and redemption process simplifies onboarding.
B2B is included in all Azure AD editions and is essential for modern supply chain and partner ecosystems.
Azure AD B2C: Customer Identity and Access Management
Azure AD B2C is a separate service designed for managing customer identities at scale.
- Enables consumer-facing apps to support social logins (Google, Facebook, Apple).
- Customizable sign-up and sign-in user journeys.
- Billed per authentication, making it cost-effective for high-volume apps.
Note: Azure AD B2C is not the same as Azure AD B2B—it’s a distinct service with different pricing and architecture.
Identity Governance: Automating Access Lifecycle
Identity Governance in Azure AD Premium P2 helps organizations manage access at scale.
- Access reviews ensure users only have necessary permissions.
- Entitlement management automates the provisioning of access packages for projects or roles.
- Role eligibility reduces standing privileges through just-in-time activation.
These features are critical for meeting compliance requirements and reducing insider threats.
Best Practices for Deploying and Managing Azure Active Directory
Deploying Azure AD successfully requires planning, governance, and ongoing management. Here are proven best practices to ensure a secure and efficient implementation.
Start with a Clear Identity Strategy
Define your identity model: Will you go cloud-only, hybrid, or use Azure AD B2C for customers?
- Map existing on-prem AD structure to Azure AD.
- Plan UPN suffixes and domain verification.
- Define administrative roles and delegation model.
A clear strategy prevents chaos and ensures scalability.
Enable Multi-Factor Authentication for All Users
MFA is the single most effective step to prevent account compromise.
- Start with administrators, then expand to all users.
- Use the Microsoft Authenticator app for passwordless authentication.
- Consider FIDO2 security keys for high-risk roles.
Microsoft reports that MFA blocks 99.9% of automated attacks.
Implement Conditional Access Policies Gradually
Deploy Conditional Access in phases to avoid disrupting users.
- Start with a baseline policy requiring MFA for all cloud access.
- Use the “Report-only” mode to test policies before enforcement.
- Monitor sign-in logs to identify impacted users.
Gradual rollout ensures smooth adoption and minimizes helpdesk tickets.
What is Azure Active Directory used for?
Azure Active Directory is used to manage user identities, enable single sign-on to cloud and on-premises applications, enforce security policies like MFA and Conditional Access, and support hybrid identity scenarios. It’s the foundation of identity and access management in the Microsoft cloud ecosystem.
Is Azure AD the same as Windows Active Directory?
No, Azure AD is not the same as Windows Server Active Directory. While both manage identities, Azure AD is cloud-native, uses modern authentication protocols (OAuth, SAML), and is designed for cloud and hybrid environments. Traditional AD relies on LDAP, Kerberos, and on-prem infrastructure.
What’s the difference between Azure AD Free and Premium?
Azure AD Free includes basic identity and SSO features. Premium P1 adds access reviews, dynamic groups, and hybrid identity. Premium P2 includes Identity Protection, Privileged Identity Management, and advanced governance features.
How do I secure Azure Active Directory?
Secure Azure AD by enabling MFA for all users, implementing Conditional Access policies, using Privileged Identity Management for admins, monitoring sign-in logs, and conducting regular access reviews. Follow Microsoft’s Zero Trust principles for maximum security.
Can Azure AD replace on-premises Active Directory?
For many organizations, yes—especially those adopting cloud-first strategies. However, some legacy applications still require on-prem AD. Hybrid models using Azure AD Connect are common during transition phases.
In conclusion, Azure Active Directory is far more than just a cloud directory—it’s the cornerstone of modern identity management, security, and access control in the digital era.From enabling seamless single sign-on to enforcing Zero Trust security with Conditional Access and Identity Protection, Azure AD empowers organizations to thrive in a hybrid and cloud-centric world.Whether you’re managing internal employees, collaborating with external partners via B2B, or building customer-facing apps with B2C, Azure AD provides the tools and scalability needed.
.By following best practices—like enforcing MFA, leveraging dynamic groups, and adopting identity governance—you can build a secure, compliant, and efficient identity foundation.As cyber threats evolve and remote work becomes the norm, investing in a robust identity strategy with Azure Active Directory isn’t just smart—it’s essential..
Recommended for you 👇
Further Reading: